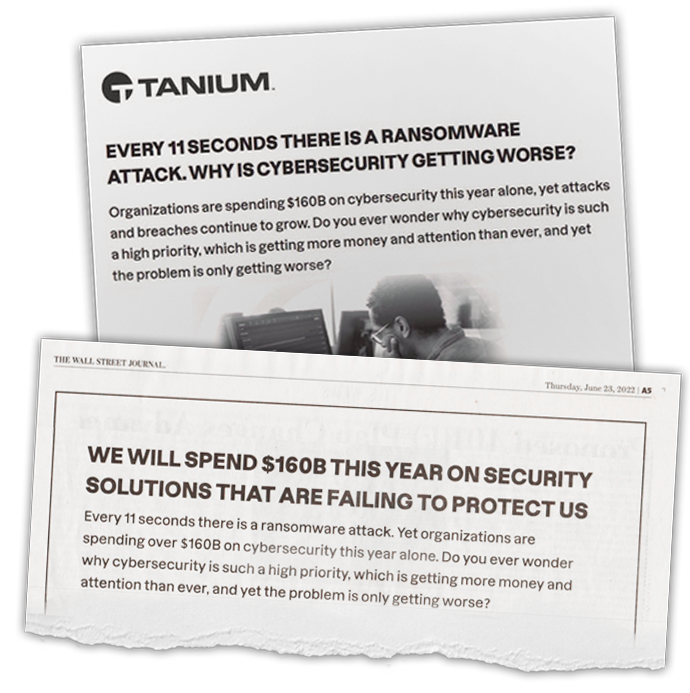

In fact, the security situation has indeed changed.
It has become much worse!
... for everyone, that is, except the vendors of security technology.


If that sounds nefarious, it didn't start out that way. Here's how security got off track back in the 1970s and started basing its solutions on a concept that has remained, to this day, the marquee strategy of the security industry ...

Here's how CTBG was born ...
Excerpt from What Happened? Wes Kussmaul narrates.

Now here's the good news
The viable solution to security challenges has been hiding in plain sight since it was created around the same time IBM was raising security concerns in the '70s.
It starts with AC.
We use AC every day in things like these:

If you want, click here to read about 12 reasons
why AC has not been deployed properly.
Most important of those 12 reasons is #7:
Here's how AC works:

Get in touch with one of these Authenticity Enterprises to bring security based on personal accountability to your organization's information infrastructure.